|
Private |
E-textile Based Imaging Array: Phase Two
IntroductionThis web page describes the work done on the second phase of the project and the results obtained. We have successfully resolved the problems we experienced in Phase 1. Using token-based network control, we were able to eliminate frame collisions. All the nodes in the array have been able to construct the ID map of the entire array. However, the sensor image has not been formed up in any of the nodes as each node was not able to propagate its data beyond its neighboring nodes, potentially due to link faults.
Work DoneResolving Outstanding Issues from Phase 1 Frame collision Other Problems Arising in Phase 2 In phase 2, all the nodes have started to transmit sensor data after they complete the ID map. However, it seems that the data of each node does not propagate beyond its neighboring nodes. We have managed overcome the problem of lost tokens by implementing a time-out for nodes waiting for the token. Thus a node will not wait infinitely for a token. However, it appears that the link failure rate is very high. Apparently, it seems like we already have a reliability problem.
Current StatusIn phase 2, we managed to get the nodes to complete the construction of the ID map, which is a critical portion of the algorithm. However, the nodes were not able to receive the entire image.On the simulation aspect, the configuration script for the imaging array setup is complete. Using the simulator’s “dumppwr” commands, we were able to show the power statistics of the individual nodes, although at this point of time, the power data is not too meaningful.
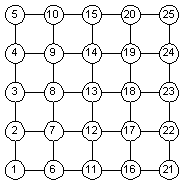
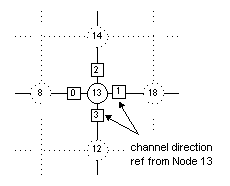
Log FilesDuring the simulation, every node outputs to an individual log file. Figure 1 shows a typical log file. The file specifically belongs to Node 13 (the complete log file for Node 13 can be found in the “Project Files” section). Figure 2 shows that distribution of the Node IDs. Note that although the IDs have been regularly distributed in this case, the algorithm does not assume that to be the case. Any distribution of IDs will work.
There are generally three types:
The second and third parts are generated by the simulator, denoting the node number and clock counts (for types 1 and 2) or energy consumed (for type 3). Looking at Figure 1, we can see that Node 13 started off by broadcasting
its own ID (sending a message Type 1). As it receives ID data from
its neighbors, e.g. a Type 1 message from Node 12, it will update
its own ID map. When it has collected information about all its
four neighbors, it will indicate this by an 'I' printout with its
neighbors’ IDs. Then, it will start to broadcast all its neighbors
IDs (Type 2 message). If it receives a similar message (i.e. Type
2), it will reroute the message (send as a Type 5 message) and update
its own ID map. When it completes building the ID map, it will start
to send out its sensor data (Type 3 message).
Next phaseThe next phase will be a continuation of the current phase. We will continue to refine the algorithm and simulation such the all nodes would be able to build up the image array. A major consideration would be the reliability of the network links.We shall also look at the power consumption of implemented architecture and explore different ways to reduce power consumption. ConclusionIn conclusion, we have successfully resolved the problems we experienced in phase 1. The imaging array is able to construct the ID map of the entire array. Using token-based network control, we were able to eliminate frame collisions. However, the sensor image cannot be formed up yet, potentially due to link faults in the network.References[1] “A Survey of Technologies for Smart Fabrics(Computational Textiles), DRAFT, Summer 2001”, Phillip Stanley-Marbell[2] “Project proposal, E-Textile-based Ultra-sound Imaging Array”, Seng Teck, Sing & Chee Wan, Teng [3] “Project Report Phase 1, E-Textile-based Ultra-sound Imaging Array”, Seng Teck, Sing & Chee Wan, Teng [4] “Myrmigki Simulator Manual, Release 0.1.ece743”, Philip Stanley-Marbell.
|
|||||||||
|
||||||||||