Biometric Recognition Research
Interests
Verifying the identity of a user is critical for many security applications such as e-commerce, access control and surveillance. Most current authentication systems are password based, making them susceptible to problems such as forgetting the password and passwords being stolen. One way to overcome these problems is to employ biometrics (e.g., fingerprints, face, iris, voice, etc.) for authentication. Biometric authentication refers to the task of matching a stored biometric to a live biometric and deciding whether their match quality is good enough or not. Authentication finds many applications such as access control and identity verification. A related problem is biometric identification where the live biometric is compared to a database of stored biometric to determine the identity of the individual whose live biometric is presented. Biometric identification may be of more interest in applications where an unknown or uncooperative is to be identified.
A major challenge in biometric recognition is overcoming their normal variability. For example, appearance of a face can change significantly with changes in expressions, illuminations and pose. Our research is focused on performing biometric verification robustly even in the presence of normal variability. Towards this task we are developing and evaluating advanced correlation filters that are capable of synthesizing few filters that capture the variability in a set of training images. We are currently investigating the use of correlation filters for the recognition of the following biometrics.
· Face images
· Fingerprint images
· Iris images
· Voice patterns
Our tests indicate that correlation filters are well suited
for biometric recognition. When tested with CMU's AMP Labs facial expression
database (15 subjects with 75 facial expressions per subject) and the
illumination subset of the PIE database (on 65 subjects), correlation filters
yield no verification errors, in certain circumstances using as few as 3
training images to design the correlation filter. Similarly, better than 0.5%
equal error rates are achieved on the NIST-24 fingerprint database and no
verification errors were observed when tested on a small database of 9 iris
images.
References:
B.V.K. Vijaya Kumar, M. Savvides, K. Venkataramani and C. Xie, “Spatial frequency domain image processing for biometric recognition,” Proc. of Intl. Conf. on Image Processing (ICIP), Vol. I, 53-56, 2002.
M. Savvides, B.V.K. Vijaya Kumar and P. Khosla, "Face verification using correlation filters," Proc. Of the Third IEEE Automatic Identification Advanced Technologies, 56-61, Tarrytown, NY, March 2002.
C. Soutar, D. Roberge, A. Stoianov,
R. Gilroy and B.V.K. Vijaya Kumar, "Biometric Encryption," Chapter 22
in ICSA Guide to Cryptography, edited by Randall K. Nicholls, 649-675,
1999.
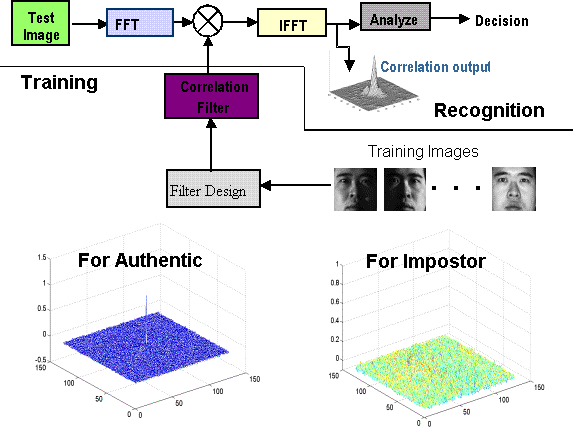
A schematic of how correlation
filters are designed and used for biometric (e.g., fingerprint)
verification. During the enrollment stage, a few variants of the
user’s biometric are collected and processed to create a correlation
filter. This filter is stored and used during the verification stage
to verify the authenticity of the live biometric provided. The output
during the verification stage is a correlation output that exhibits a
sharply peak when the input is from an authentic user (bottom left) and no
discernible peak when the input biometric is from an impostor (bottom
right).